Cybersecurity Assessment (EU Act) - DYMO LabelWriter Wireless
Security assessment of a consumer IoT device following ETSI EN 303 645 standards.
Grade: 7.5
Cybersecurity Assessment - DYMO LabelWriter Wireless
During our cybersecurity lab at HAN University of Applied Sciences, Len Verploegen and I conducted a security assessment of a consumer device following the ETSI EN 303 645 standard. We chose the DYMO LabelWriter Wireless, a thermal label printer that connects via Wi-Fi.
Device Under Test
- Product: DYMO LabelWriter Wireless thermal label printer
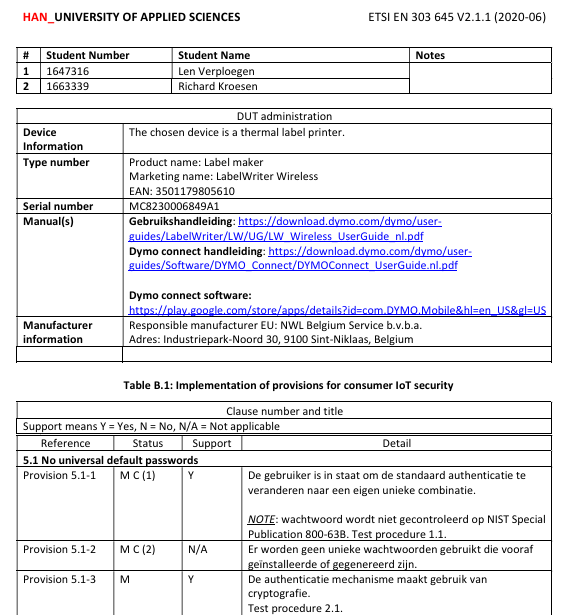
- Model: MC8230006849A1
- Manufacturer: NWL Belgium Service b.v.b.a.
Assessment Results
✅ Security Strengths
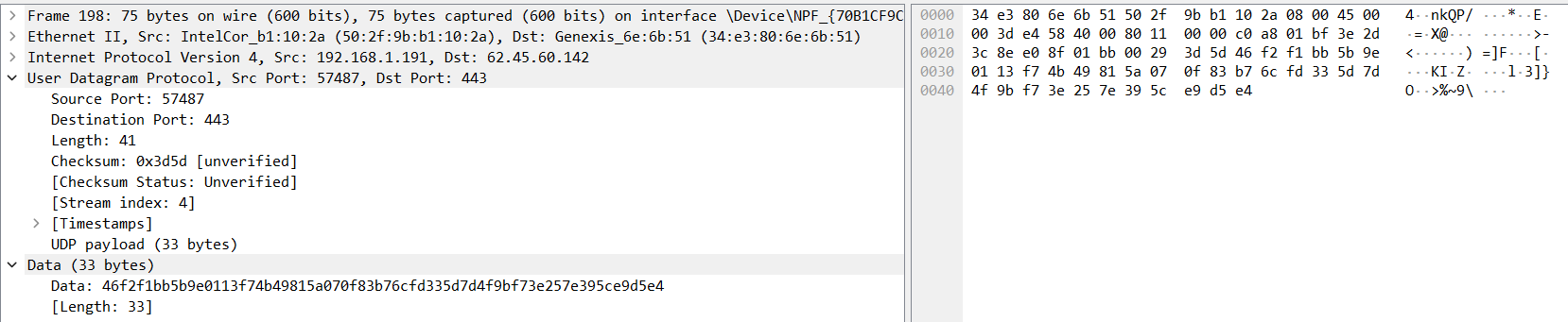
- Encrypted Communication: All network traffic properly encrypted (verified via Wireshark)
- Authentication Required: Users can change default credentials with cryptographic protection
- Network Security: Supports WPA/WPA2 and secure WPS implementation
- Access Control: Configuration only accessible via local network
⚠️ Critical Vulnerabilities
- Weak Password Policy: Accepts single-character passwords
- No Rate Limiting: Unlimited login attempts allowed - brute force attacks possible
- Poor Update Management: Broken firmware update links and unclear support timeline
- Missing Vulnerability Disclosure: No coordinated disclosure process documented
Testing Methodology
Our assessment included:
- Network Analysis: Wireshark packet capture and encryption verification
- Hardware Inspection: PCB analysis using oscilloscope
- Penetration Testing: Brute force attempts and configuration testing
- Documentation Review: Manual and policy analysis
Illustrates first page of the document, just to give an idea of the content.
Key Finding: Password Weakness
The most concerning discovery was the password implementation. Despite requiring authentication, the system accepts passwords as short as one character, creating a significant security risk.
Compliance Summary
Out of applicable ETSI EN 303 645 provisions:
- ✅ 15 provisions: Compliant
- ⚠️ 6 provisions: Non-compliant
- ℹ️ 12 provisions: Not applicable
Recommendations
For Users:
- Change default credentials immediately
- Use strong passwords despite system limitations
- Monitor network activity regularly
For Manufacturers:
- Implement proper password complexity requirements
- Add authentication rate limiting
- Establish clear vulnerability disclosure processes
Technologies Used
- Standard: ETSI EN 303 645 V2.1.1
- Tools: Wireshark, oscilloscope
- Testing: Network analysis, hardware inspection, penetration testing
Conclusion
This lab demonstrated that even simple IoT devices like label printers can introduce serious security risks. While the DYMO printer implements several good security practices, critical weaknesses in password policy and update management create significant vulnerabilities that could be exploited by attackers.
The assignment reinforced the importance of comprehensive security evaluation for all connected devices, regardless of their perceived simplicity.
This project was completed as part of the Security Lab (EMBSYD02-Security) course at HAN University of Applied Sciences, Embedded Systems Engineering program, S4 2022-2023.